A few members have reported over the last week that when they come on my website, their antivirus suite is issuing a warning that there's a virus on my site.
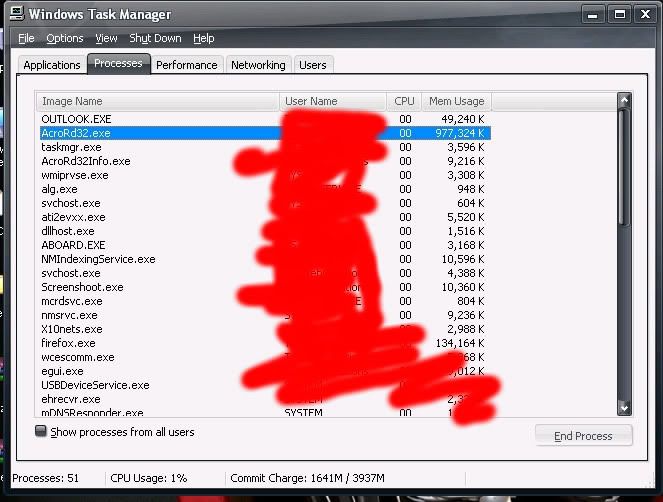
Nod32 is not showing any problems when I view the site- However.. when you go onto this site AcroRd32.exe starts, and it's hogging up memory resourses big time.
See screenshot on my PC:
Only things I've installed lately are:
Dock in Rock
Classifieds
VBTubePro
Any help will be most appreciated with this, before I start losing valued members
Nod32 is not showing any problems when I view the site- However.. when you go onto this site AcroRd32.exe starts, and it's hogging up memory resourses big time.
See screenshot on my PC:

Only things I've installed lately are:
Dock in Rock
Classifieds
VBTubePro
Any help will be most appreciated with this, before I start losing valued members
